FEATURES
Agentic AI Workflows
Zynap, the only agentic AI-powered platform that turns threat intel into instant, context-aware response, from detection to action.



CONNECT
Unify tools, teams, data and processes
AUTOMATE
Intelligent, context-aware automation
EMPOWER
Amplify existing capabilities
TEAMS
Improve collaboration and efficiency
TOOLS
Maximize investment in existing tools
DATA
Unlock full power of telemetry and threat intel
PROCESSES
Streamline and automate security operations
Your SOC without silos. Your data without limits. Your team without burnout.
Zynap unifies it all as the brain behind your security stack, giving your teams the speed, context, and collective intelligence to anticipate and respond to any threat in real time.



CONNECT
Unify tools, teams, data and processes
AUTOMATE
Intelligent, context-aware automation
EMPOWER
Amplify existing capabilities
TEAMS
Improve collaboration and efficiency
TOOLS
Maximize investment in existing tools
DATA
Unlock full power of telemetry and threat intel
PROCESSES
Streamline and automate security operations
Your SOC without silos. Your data without limits. Your team without burnout.
Zynap unifies it all as the brain behind your security stack, giving your teams the speed, context, and collective intelligence to anticipate and respond to any threat in real time.
Key Features
The Engine Behind Proactive Security
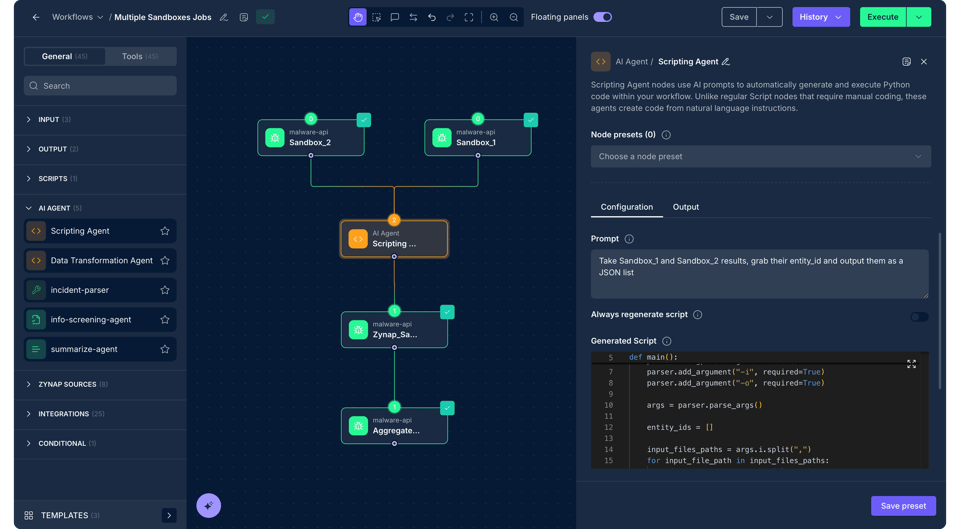
At the heart of Zynap, Michelangelo powers a new era of security operations, an AI-driven workflow engine built to think faster, automate smarter, and act with precision.
Michelangelo eliminates the complexity of traditional automation by fusing expert logic and no-code simplicity, enabling any security team, from new analysts to seasoned veterans, to design, optimize, and execute sophisticated workflows with speed and confidence. Simply drag and drop the visual components to draw the desired workflow and the business logic and code is developed for you.
In today’s high-stakes environment, Michelangelo enables teams of any skill level to achieve operational excellence.
Overwhelmed and Underprepared
Cybersecurity teams are overwhelmed with an ever-growing number of threats, alerts, and compliance requirements. Manual processes slow down response times, increase the risk of human error, and make it difficult to keep up with evolving threats.
Smarter Cybersecurity Operations
To overcome these challenges, organizations need an intelligent, automated approach to cybersecurity operations. Our platform helps security teams streamline processes, reduce manual effort, and enhance threat response capabilities.
Integrated Internal Intelligence Sources
Built on 20+ years of experience on the frontlines of cybersecurity, Zynap brings deep operational expertise that goes far beyond our proprietary threat intelligence. We fuel unmatched attacker insights into every security workflow — not just through our data, but by enhancing how threat intelligence is prioritized, interpreted and operationalized across the tools you already use.



Credentials Intelligence
Beyond traditional credential leak detection, Zynap delivers session intelligence, navigation profiling, and dynamic identity analysis — combining credential data, session behaviors, and device profiles to offer unparalleled context and proactive defense.


Malware Intelligence
Leveraging our next-generation, threat intelligence-driven sandbox, Zynap reinvents malware analytics — making deep malware analysis not only more powerful but also accessible to all security teams, regardless of technical background.

External Attack Surface Management (EASM)
Zynap provides full visibility into your exposed and hidden attack surfaces, identifying known vulnerabilities, as well as unknown or newly emerging assets that require urgent action and validation.
Integrated Internal Intelligence Sources
Built on 20+ years of experience on the frontlines of cybersecurity, Zynap brings deep operational expertise that goes far beyond our proprietary threat intelligence. We fuel unmatched attacker insights into every security workflow — not just through our data, but by enhancing how threat intelligence is prioritized, interpreted and operationalized across the tools you already use.

Credentials Intelligence
Beyond traditional credential leak detection, Zynap delivers session intelligence, navigation profiling, and dynamic identity analysis — combining credential data, session behaviors, and device profiles to offer unparalleled context and proactive defense.

Malware Intelligence
Leveraging our next-generation, threat intelligence-driven sandbox, Zynap reinvents malware analytics — making deep malware analysis not only more powerful but also accessible to all security teams, regardless of technical background.

External Attack Surface Management (EASM)
Zynap provides full visibility into your exposed and hidden attack surfaces, identifying known vulnerabilities, as well as unknown or newly emerging assets that require urgent action and validation.
Challenges We Solve
Fragmented security ecosystems
Unified orchestration across teams, tools and data.
Manual workloads
Automated, intelligent workflows save time and reduce errors.
Burnout and alert fatigue
Smart prioritization and targeted actions free analysts from noise.
Operational silos
One language across teams, one platform across tools.
Vendor lock-in
Freedom to easily evolve your technology stack.
Reactive log dependency
Proactive actions anticipate threats rather than just react to alerts.
MSSP-ready by design
Delivers a modular, scalable path from MSSP to full MDR capabilities.
Static, disconnected compliance efforts
Automated security validation mapped to MITRE, NIST, ISO27001, DORA, and NIS2.

See the impact. Feel the difference.
Book a demo now and witness firsthand how Zynap's intelligent automation revolutionizes team collaboration, dramatically boosting both the efficiency and impact of your entire cybersecurity program.
Book a demo