Product
Solutions
Company
From Intel to Action
AI-driven threat intel that unifies data sources to turn raw intel into real-time action, enabling preemptive security at scale through attack prevention, faster response, and stronger defenses.
Trusted by Pioneers in Prevention

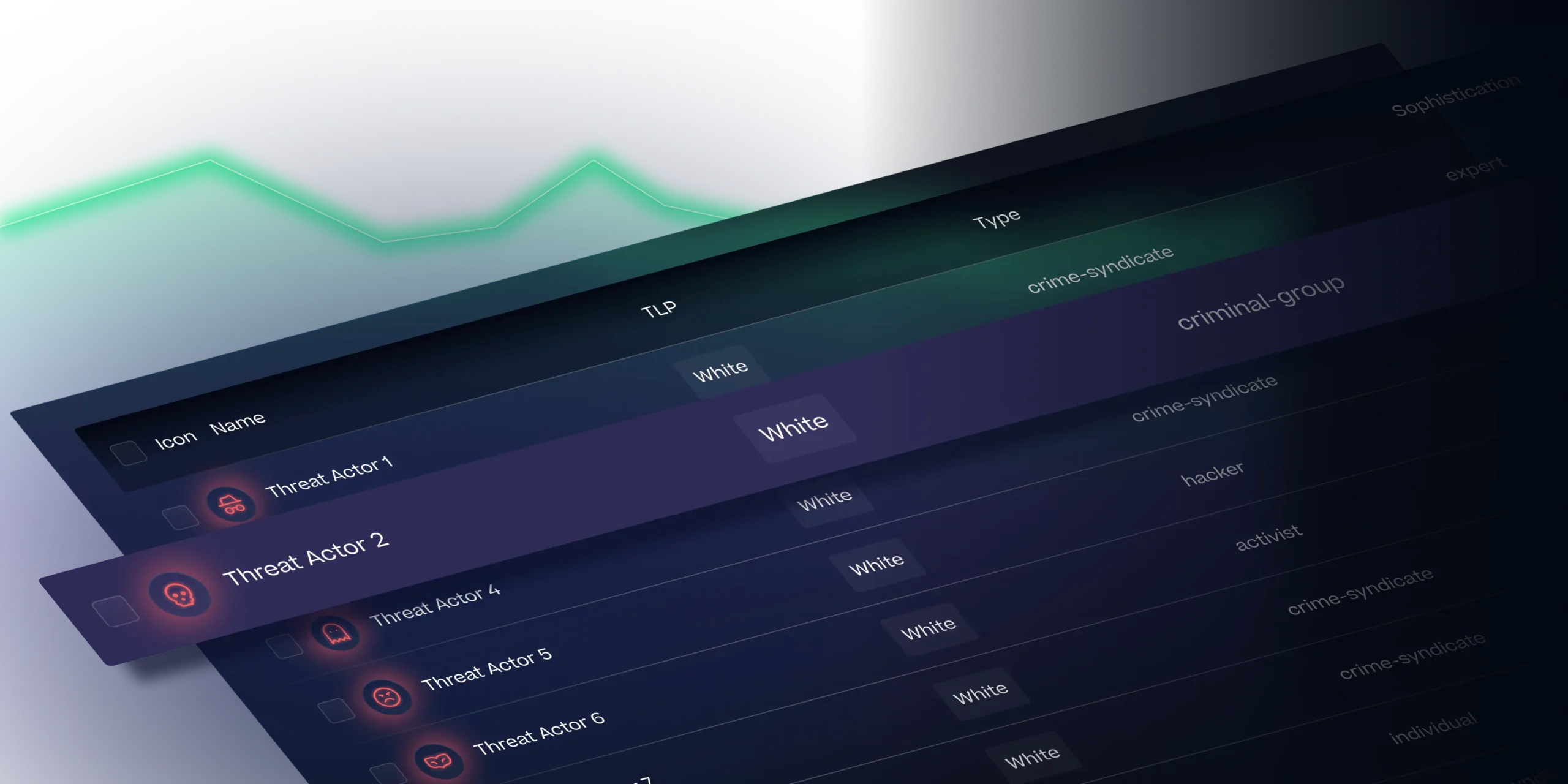
Threat Intelligence Platform
Zynap’s agentic AI-powered platform turns raw threat data into actionable foresight to simulate and prevent attacks before they happen.
Boost analyst capacity by eliminating repetitive tasks, enabling focus on meaningful threat intelligence investigations.
Simulate real adversary tactics to uncover weaknesses, protect critical assets, and provide evidence for stronger, proactive security measures.
Transform alert enrichment into active defense by leveraging threat intelligence to guide investigation, response, and proactive prevention.
Gain access to a proprietary malware sandbox that extracts unique intelligence from in-depth sample analysis.
Turn Intelligence into Clarity
Turn threat intel from an array of internal and external sources into real-world action -processing, correlating, and prioritizing- threats instantly.
Insights Delivered 24/7
+300K
Total CVEs identified and updated in our database
+900
Total threat actors profiled
+20K
Total exploits and POCs identified for vulnerabilities.
+25K
Total victims of tracked threat actor campaigns
Our team tracks real attacks, learns how they spread, and turns it into intel that helps you stay ahead.
Zynia Labs enriches public intelligence by combining automated collection systems with original targeted investigations into campaigns, actors, and malware, feeding Zynap with fresher, deeper context.
Hands-on analysis of live malware and attacker tooling ensures your automation, detections, and simulations are grounded in how adversaries actually operate today.
Focus research on the threat actors that matter most, following their infrastructure, tools, and campaigns over time with curated, analyst-led investigations.
Our Solutions
Transform external intel into immediate action for clients.
Enhance client defenses with safe, AI-powered adversary simulations enriched by real threat intelligence context.
Go beyond basic detection and response to deliver faster, more consistent, and fully contextualized protection.
Capabilities
Validate credentials, spot true exploits, and act with instant threat context.
Learn moreBuild workflows fast with low-code tools, AI agents, and a collaborative canvas.
Learn moreBoost smarter, faster, scalable security with AI agents that adapt and automate.
Learn more